
Here’s a collection of tools I commonly use for exploiting embedded systems together with an installation guide. This post will be updated regularly, to include the latest scripts and tools.
GDB Debugger
For debugging I recommend the GNU Arm Embedded GCC binaries from xpack-dev-tools/arm-none-eabi-gcc-xpack. Download the the latest release (e.g. xpack-arm-none-eabi-gcc-10.3.1-2.3-linux-x64.tar.gz) and unpack it.
mkdir -p ~/opt/xPacks/arm-none-eabi-gcc
cd ~/opt/xPacks/arm-none-eabi-gcc
tar xvf ~/Downloads/xpack-arm-none-eabi-gcc-10.3.1-2.2-linux-x64.tar.gz
chmod -R -w xpack-arm-none-eabi-gcc-10.3.1-2.2
In the following, the gdb binary with python support (arm-none-eabi-gdb-py3) is used. It is located in arm-none-eabi-gcc/xpack-arm-none-eabi-gcc-10.3.1-2.2/bin/
GDB with GEF
GEF is a set of commands to assist exploit developers and reverse-engineers when using old school GDB. It provides additional features to GDB using the Python API to assist during the process of dynamic analysis and exploit development.
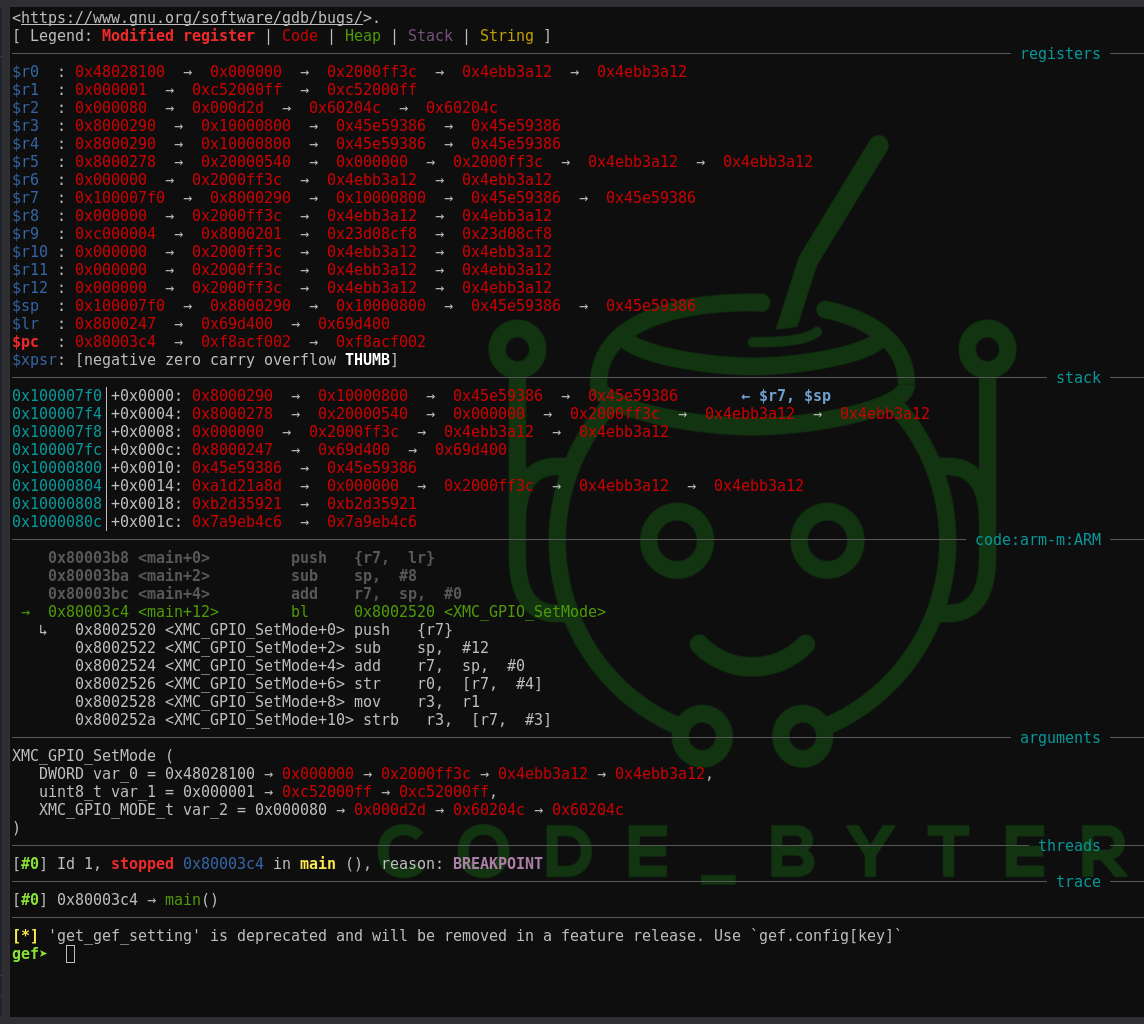
To install GEF, clone the repository and create the ~/.gdbinit file with the source command for gef in the respective directory.
git clone https://github.com/hugsy/gef.git
# Create the new gdbinit
echo "source /path/to/gef/gef.py" > ~/.gdbinit
For ARM Cortex M support, we need to install gef-extras. Gef-extras is an open repository of external scripts and structures to be used by GEF. To install it, run the installation script in the gef/scripts directory and add the source command for the CPU architecture to the ~/.gdbinit file.
bash /path/to/gef/scripts/gef-extras.sh
# Create the new gdbinit
echo "source ~/.config/gef-extras/archs/arm-cortex-m.py" >> ~/.gdbinit
When you launch the arm-none-eabi-gdb-py3 debugger, you should see the GEF interface. All you need to do no, is set your architecture manually by the following command in the gef prompt:
gef➤ python set_arch('ARM-M')
Ropper
A binary exploitation challenge wouldn’t be fun, if the stack is executable. For return oriented programming, finding gadgets to use can be automated.
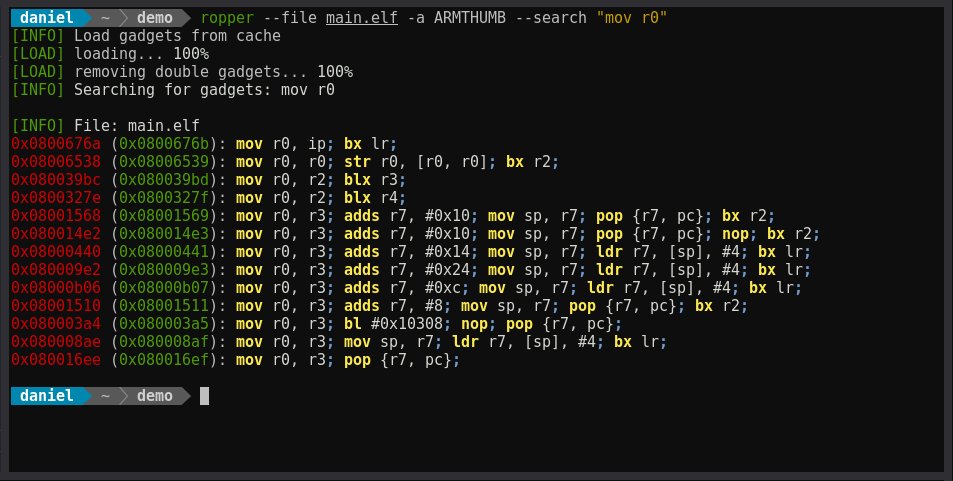
Ropper displays information about binary files in different file formats and you can search for gadgets to build rop chains for different architectures.
It can be installed with pip.
sudo pip install capstone
sudo pip install filebytes
sudo pip install keystone-engine
pip install ropper
You can now use it to print all available gadgets or search for specific ones.
ropper --file main.elf -a ARMTHUMB --search "mov r0"
Ghidra Software Reverse Engineering Framework
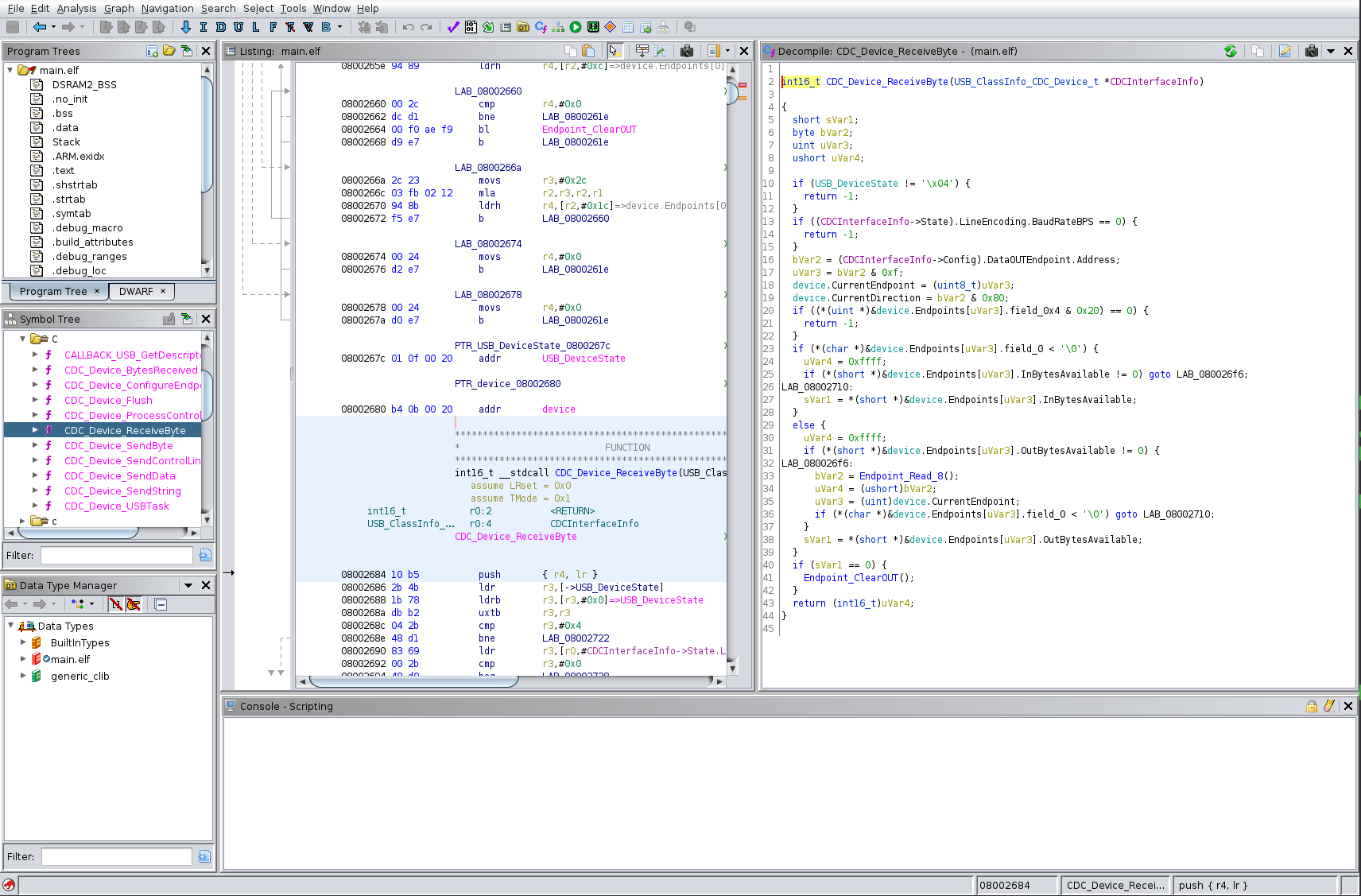
Ghidra is a reverse engineering framework created and maintained by the National Security Agency Research Directorate. It includes software analysis tools that help to analyze compiled code. Capabilities include disassembly, assembly, decompilation, graphing, and scripting. It helps to get an overview which functionalities are available within your binary and how specific functions are implemented.
