
This blog post investigates the security of a doorbell with an integrated WiFi camera. An unauthenticated attacker within the network can perform a Man-in-the-Middle attack and get unauthorized access to the camera’s life video feed, and trigger the doorbell remotely
Wireshark Packet Analysis
Setup: Mitm attack on the WiFi Doorbell. This can be done for example by creating a WiFi hotspot that is traced with wireshark and connecting the WiFi Doorbell to it.
The wireshark captures show the following characteristics
- TCP Packets for ringing the doorbell and initiating the Live Video Stream
- UDP Packets for the raw video stream
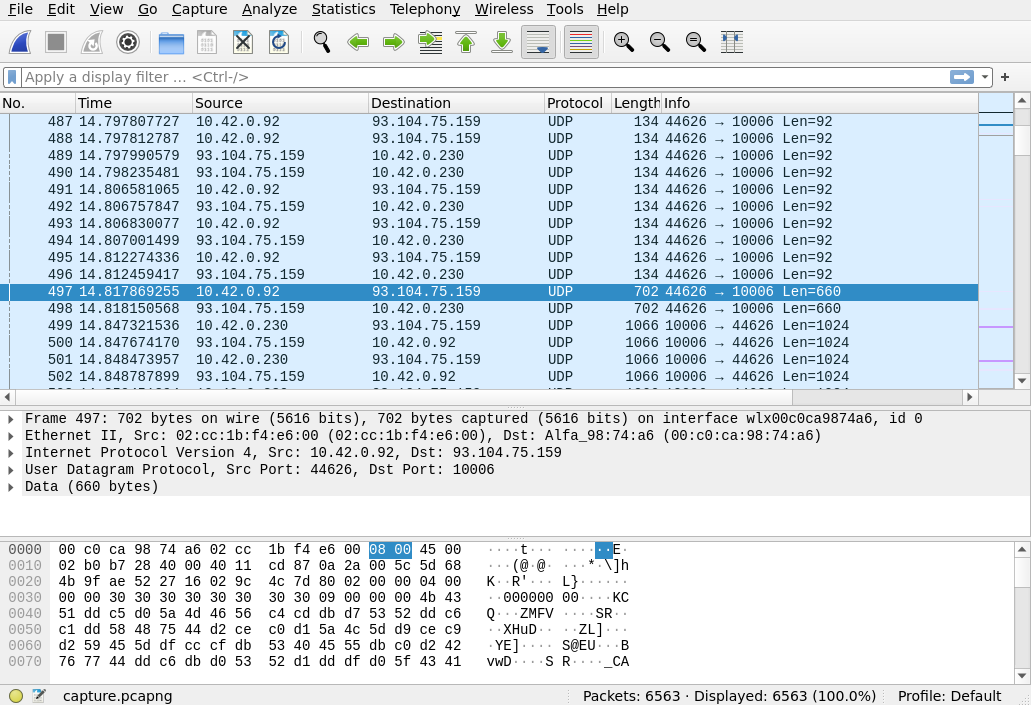
When following the full captured UDP stream, the keywords JFIF can be found. The JFIF (JPEG File Interchange Format) is a standard format for storing and exchanging compressed digital images, and it is essentially the same as the JPEG (Joint Photographic Experts Group) format but with added metadata.
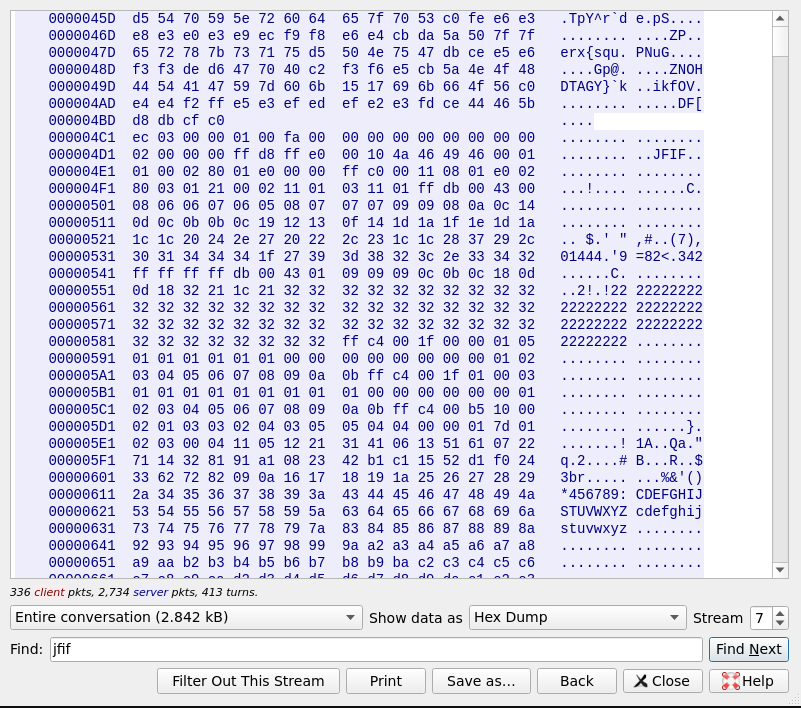
The JFIF file header has the following structure. It starts with 6 bytes of data and then contains JFIF as null terminated string. These can be found in the raw UDP stream in regular intervals.
This shows, the UDP stream consists of stream of JFIF images which compose the video stream.
Decoding the live video stream
The video stream can be easily reconstructed via a python. First the UDP packages are joint together to form a stream. Afterwards, for each JFIF header, the image can be shown using the Python Imaging Library PIL.
