
This blog post investigates the security of a doorbell with an integrated WiFi camera. The Bluetooth communcication between the companion app and the doorbell is unecrypted and can be sniffen. This allows an unauthenticated attacker to gain access to your local WiFi network.
Pairing Process
The doorbell generally communicated via the WiFi network. However for initial pairing, the WiFi credentials are transmitted via BLuetooth Low Energy. Once the pairing process is completed, bluetooth is disabled on the device. This blog posts investigates the security of the Bluetooth Communication during the pairing process.
Analysis of the communication
For initial analysis of the Bluetooth Communication, it is useful to access the Bluetooth HCI snoop logs on the Android phone. This is the preferable approach for recon as it is the most reliable one. Once you have enabled the Bluetooth HCI snoop log option in the developer settings, you can export the trace file for wireshark using adb.
adb bugreport bugreport.zip
Alternatively you can access the logs live in wireshark:
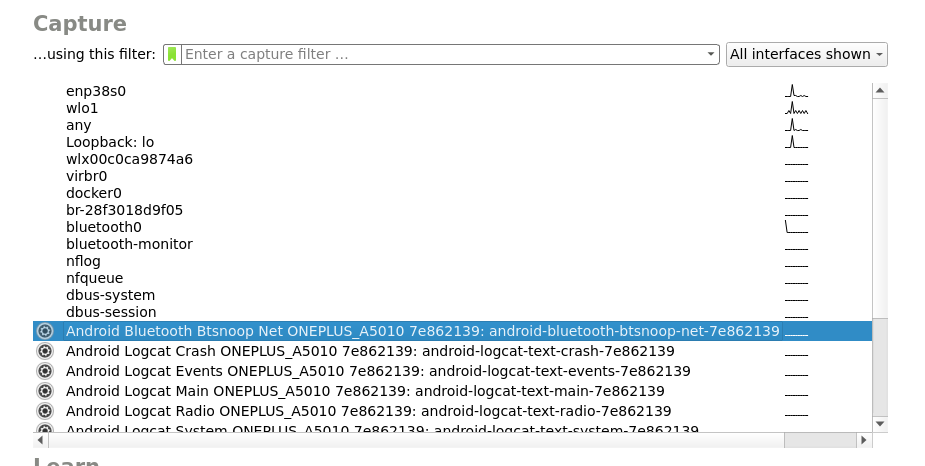
The doorbell implements Bluetooth Low Energy, therefore the relevant traffic can be extracted using the btatt filter in Wireshark.
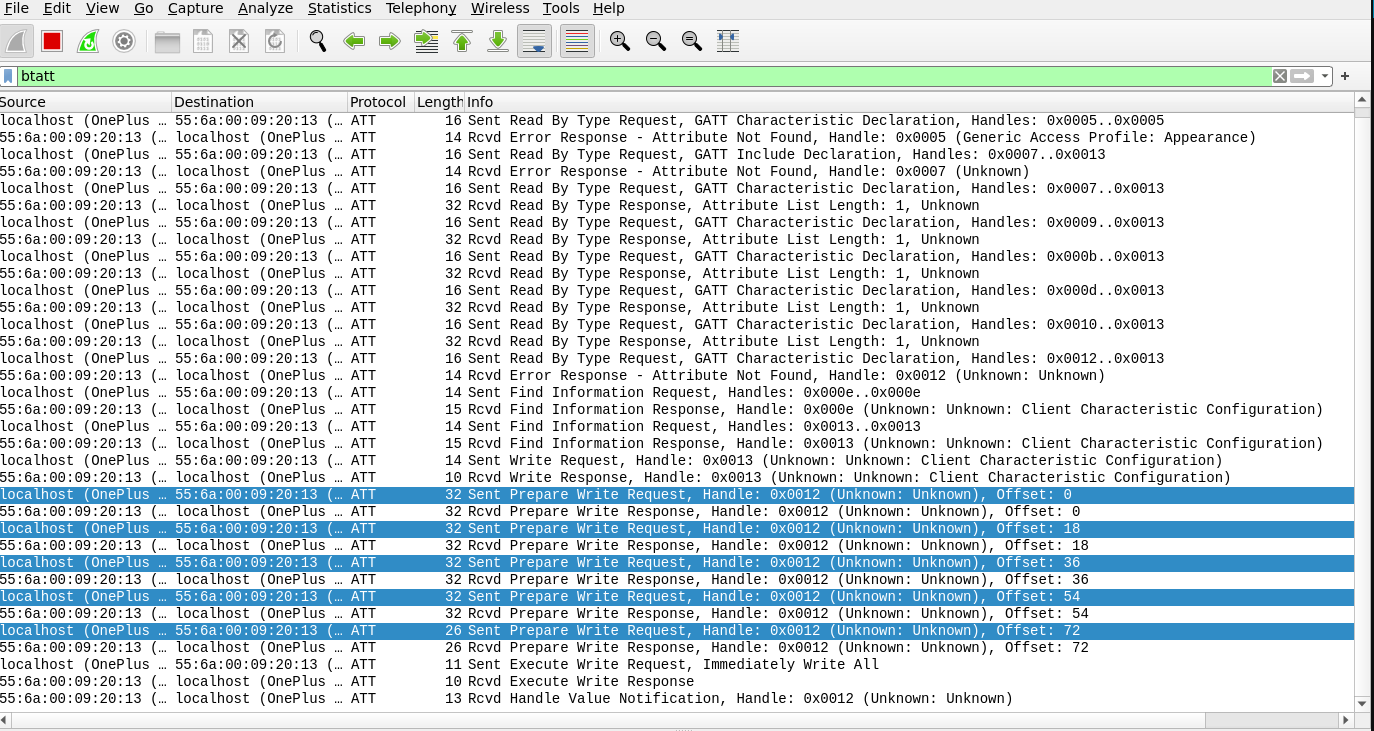
The following marked Write Requests send data from the companion app to the doorbell. As seen in the following capture, the packets contain sensitive data
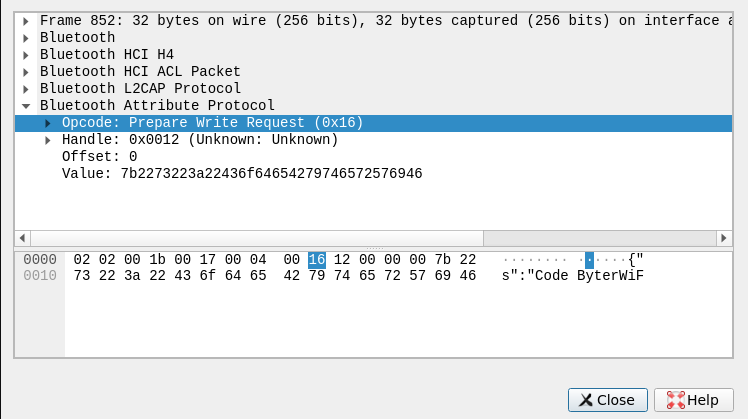
The packages can be combined to a json datastructure containing the WiFi SSID s, password p and the user-id u.
{
"s":"CodeByterWiFi",
"p":"follow_code_byter",
"u":"touristd1g51ct9e226545d94f81h7gb"
}
Once the network access credentials are transmitted, bluetooth (advertising) is disabled. Therefore the attacker has to sniff the credentials during pairing.
Sniffing the communication
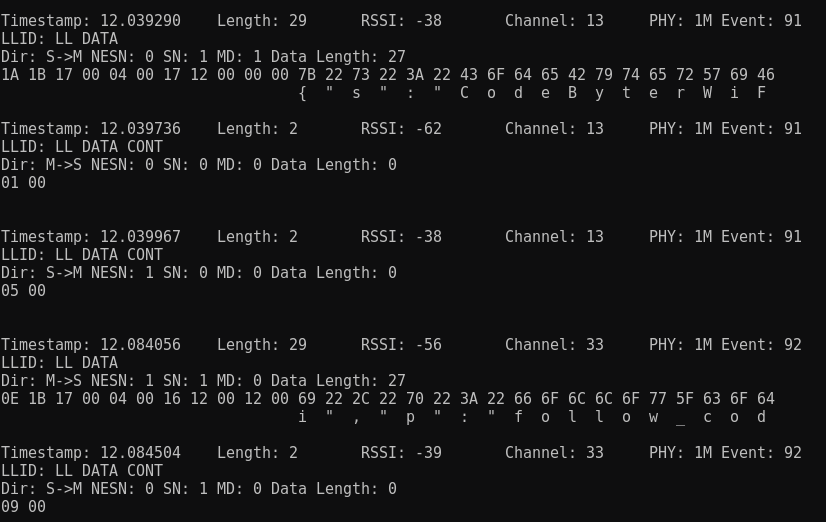
After having identified sensitive data being transmitted unencrypted via Bluetooth Low Energy, Sniffle can be used to sniff the packages, it needs to be sniffed out of the air to be exploitable.
python3 sniff_receiver.py -m <MAC-Addr> -c 37 -e
Impact
The missing encryption of the Bluetooth communication allows any aunauthenticated attacker to gain access to your local network. While this does not directly give you further access to devices, the attaacker can perform mitm attacks on any communication in your local network. Therefore the next blogpost investigates the network communcation of the smart doorbell.
